This quick reference page provides a summary of the specifications of this topology. For a complete reference including installation details, please refer to the configuration guide listed below.
| Topology | Supports | Documentation |
|---|---|---|

|
Cybersecurity Fundamentals | Cybersecurity Fundamentals v1.0 Installation and Configuration Guide |
You may request virtual machine templates for the Cybersecurity Fundamentals pod from CSSIA.
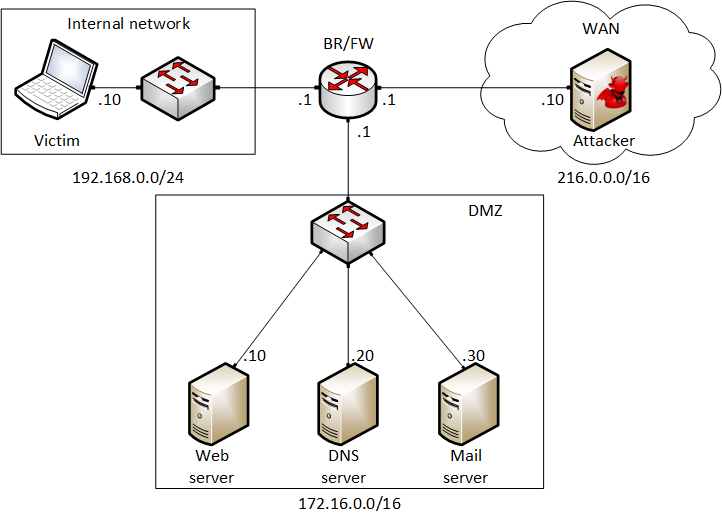
The virtual machines in the pod are listed in the table below.
| Virtual Machines |
|---|
| Attacker |
| BR/FW |
| DNS Server |
| Mail Server |
| Victim |
| Web Server |
The virtual machines are made available as Open Virtualization Format (OVF) or Open Virtualization Archive (OVA) files. These files are available for download from EPNC (Education Pathway National Center).
To request access to the preconfigured virtual machine templates from EPNC: