
This quick reference page provides a summary of the specifications of this topology. For a complete reference including installation details, please refer to the RING Cybersecurity Exploration Pod Planning and Installation Guide .
The RING Cybersecurity Exploration Pod is
designed to have internet access.
Due to the security and legal implications regarding accessing the
Internet from within the pod, we require that NETLAB+ customers indicate their acceptance of
the NETLAB+ Pod Internet Access and Use Agreement
prior to obtaining access to the pod or content for this course.
| Topology | Supports | Documentation |
|---|---|---|
 |
RING Cybersecurity Exploration Pod Planning and Installation Guide |
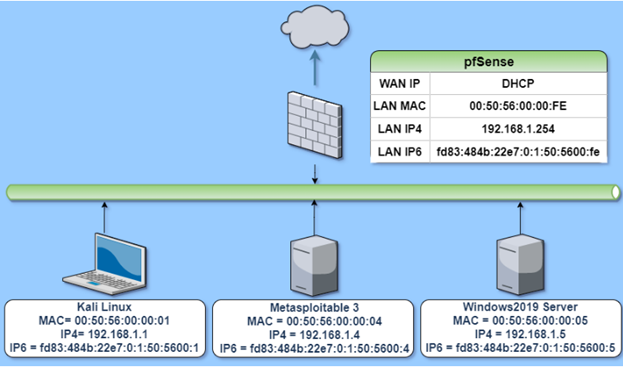
The virtual machines in the pod are listed in the table below.
| Virtual Machine |
|---|
| pfSense |
| Kali Linux |
| Metasploitable 3 |
| PodEGW |
| Windows 2019 Server |