This quick reference page provides a summary of the specifications of the CSSIA Windows 10 Administration Pod.
The CSSIA Windows 10 Administration Pod is a 100% virtual machine pod consisting of 3 virtual machines. Linked together through virtual networking, these virtual machines provide the environment for a student or team to perform the Windows10 Administration labs.
| Topology | Supports... | Documentation |
|---|---|---|
CSSIA Windows 10 Administration Pod
|
You may request virtual machine templates for the CSSIA Windows 10 Administration Pod from CSSIA.
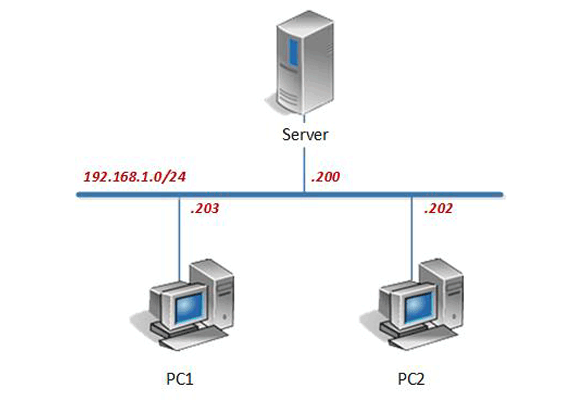
The virtual machines in the CSSIA Windows 10 Administration Pod are listed below. The Virtual Machine Deployment Names are provided as a suggested naming convention.
| Virtual Machine Topology Name | Virtual Machine Deployment Name |
|---|---|
| Server | CSSIA_WIN10ADM_Master_Server |
| PC1 | CSSIA_WIN10ADM_Master_PC1 |
| PC2 | CSSIA_WIN10ADM_Master_PC2 |
The Windows 10 Administration course will consume 26.1 GB of storage per each user pod instance.
Details of the storage requirements for each of the lab virtual machines in the CSSIA Windows 10 Administration Pod are provided in the table below. Some fluctuation in the numbers may occur.
| Virtual Machine | OVF/OVA | Initial Master Pod (thin provisioning) GB |
|---|---|---|
| Server | 3.97 | 7.4 |
| PC1 | 5.06 | 9.9 |
| PC2 | 4.47 | 8.8 |
| Total | 13.5 | 26.1 |
The virtual machines are made available as Open Virtualization Format (OVF) or Open Virtualization Archive (OVA) files. These files are available for download from EPNC (Education Pathway National Center).
To request access to the preconfigured virtual machine templates from EPNC: