This quick reference page provides a summary of the specifications of the EMC ISM Pod. The EMC ISM pod was designed to support the EMC Information Storage and Management (ISM) course.
The EMC ISM pod is a 100% virtual machine pod consisting of three virtual machines. Linked together through virtual networking, these three virtual machines provide the environment for a student or team to perform the EMC ISM labs.
| Topology | Supports... | Documentation |
|---|---|---|
|
EMC ISM Pod |
You may request virtual machine templates for the EMC ISM pod from CSSIA.
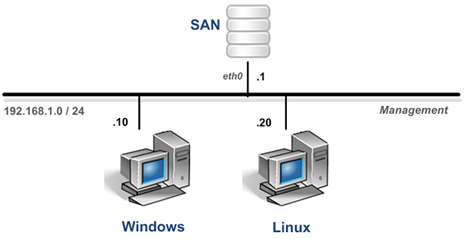
A description of the virtual machines in the EMC ISM Pod is provided in the table below.
| Virtual Machine | Role |
|---|---|
| SAN | Openfiler Storage Area Network appliance |
| Windows | A Windows client |
| Linux | A Linux client |
You should budget 8 gigabytes for each ISM master pod and 4 gigabytes each user pod instance. The datastore containing an ISM pod must be accessible to the VMware host to which it is assigned, as either directly attached local storage or a Storage Area Network (SAN).
Details of the storage requirements for each of the lab virtual machines in the ISM pod are provided in the table below. Some fluctuation in the numbers may occur.
| Lab Virtual Machines | Master Pod at Lab 0 (using full clones) |
User Pod after Last Lab(using linked clones) |
|---|---|---|
| SAN | 400MB | 3.5GB |
| Windows | 3.96GB | 4.06GB |
| Linux | 3.45GB | 3.53GB |
| Total Recommended | 8.00GB | 12.00GB |
The virtual machines are made available as Open Virtualization Format (OVF) or Open Virtualization Archive (OVA) files. These files are available for download from EPNC (Education Pathway National Center).
To request access to the preconfigured virtual machine templates from EPNC: