This quick reference page provides a summary of the specifications of the MSEC pod.

This topology was designed through a grant initiative by the Center for Systems Security and Information Assurance (CSSIA) and the Network Development Group (NDG), funded by the National Science Foundation’s (NSF) Advanced Technological Education (ATE) program Department of Undergraduate Education (DUE) Award No. 0702872 and 1002746. The topology is designed to be used with a series of lab exercises mapped to CompTIA Security+® domains.
| Topology | Supports... | Documentation |
|---|---|---|
MSEC Pod
|
You may request virtual machine templates for the MSEC pod from CSSIA.
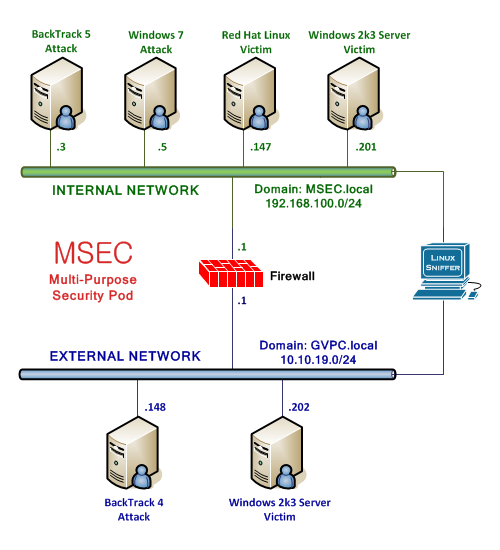
A description of the virtual machines in the MSEC Pod is provided in the table below.
| Virtual Machine | Role |
|---|---|
| BackTrack 5 Attack | BackTrack 5 |
| Windows 7 Attack | Microsoft Windows 7 Professional |
| Red Hat Linux Victim | Microsoft Windows 2003 Server (internal network) |
| Windows 2k3 Server Victim | Microsoft Windows 2003 Server |
| pfSense Firewall | Firewall |
| Sniffer | Linux based Sniffer |
| BackTrack 4 Attack | BackTrack 4 |
| Windows 2k3 Server Victim | Microsoft Windows 2003 Server (external network) |
The virtual machines are made available as Open Virtualization Format (OVF) or Open Virtualization Archive (OVA) files. These files are available for download from EPNC (Education Pathway National Center).
To request access to the preconfigured virtual machine templates from EPNC: