Ideally, NETLAB+ should be placed on a public network or DMZ. Since a NETLAB+ system might be installed behind a firewall, many steps have been taken to make NETLAB+ secure and firewall friendly. However, it is likely that some TCP/IP ports will need to be opened through the firewall.
Connection to a local area network is provided by a 10/100/1000 Ethernet connection.
NETLAB+ must have access to an Internet connection. Actual bandwidth usage varies based on the number of simultaneous connections and connection types.
Use caution with Cable and DSL solutions. Keep these issues in mind:
A fixed IP address is required for the server. DHCP is
not supported.
Many service offerings do not provide the same bandwidth
in both directions; they are usually optimized for downloads
from the Internet (inbound). For NETLAB+, it is desirable
to have more bandwidth from the server towards the Internet (outbound).
NETLAB+ will work with Static NAT.
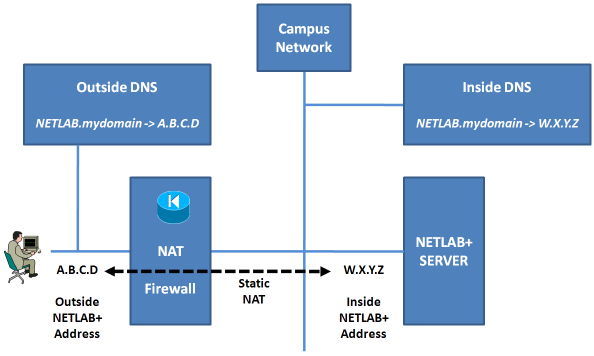
Users connect to the NETLAB+ server via the outside interface IP address. NETLAB+ listens for connections on three TCP ports. The following ports should be open in the site firewall for outside NETLAB+ access (unless all NETLAB+ users have VPN access to the site).
| Ports | Usage |
|---|---|
| TCP 80 | Web-based user interface. |
| TCP 2201 (default) |
Remote Access Port for lab equipment access and remote PC access.
|
| TCP 22 (recommended) |
SSH access for NDG staff. Contact NDG technical support to obtain the source IP address. |
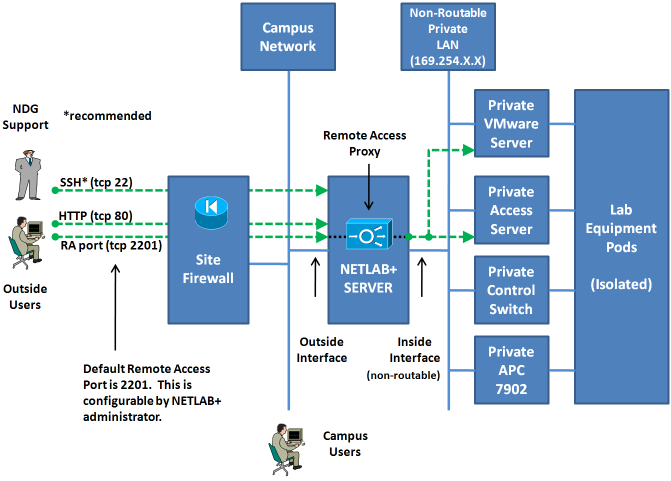
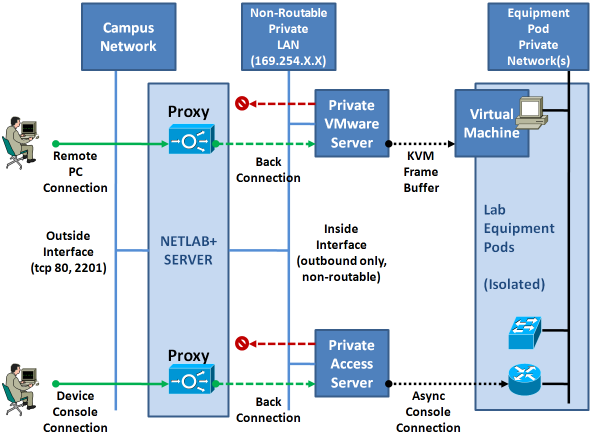
NETLAB+ provides remote access to lab equipment and remote PCs behind the NETLAB+ server. Remote access connections are performed over the Remote Access Port (described in section 1.4). Please refer to the illustration below. Several security layers are implemented to provide complete isolation between lab equipment and production networks.
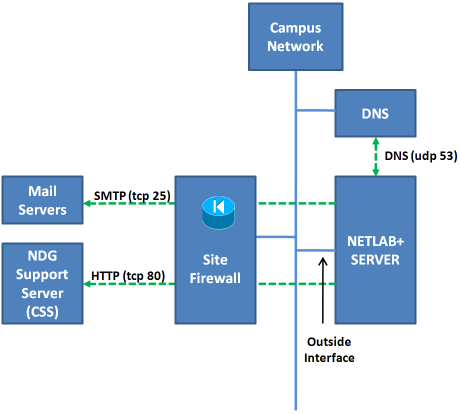
Refer to the diagram below. A NETLAB+ server makes limited outbound connections using the following ports.
| Ports | Usage |
|---|---|
| TCP 25 | Allows NETLAB+ to send e-mail to users. This is optional. |
| TCP 80 | Allows the NETLAB+ server to connect to the NDG Central Support Server. This server provides software updates. |
| UDP 53 | The NETLAB+ server makes DNS queries to resolve the address of the support server (nss.netdevgroup.com). |
Because CSS plays an important operational role, each NETLAB+ server must be able to communicate with its designated CSS server. NETLAB+ communicates with a CSS server using outbound HTTP on TCP port 80. All requests are initiated from the NETLAB+ server.
Note: There is an administrative option to redirect these requests to an HTTP proxy server. The proxy must be completely transparent. This is not officially supported by NDG. The supported method requires direct access to the Internet on TCP port 80.
NETLAB+ allows configuration of up to 2 DNS server IP addresses. If the DNS server IP addresses configured in NETLAB+ are located inside the firewall and the DNS servers perform recursive queries, it is not necessary to open outbound DNS (UDP port 53).
NETLAB+ initiates outbound e-mail on TCP port 25 to send:
If outbound SMTP mail is restricted, NETLAB+ can be configured to send mail to an alternate SMTP server address. This may not always work because policies and filters on the mail server can reject SMTP headers from NETLAB+. The supported configuration requires direct access to the Internet on TCP port 25.
NDG may require access to the NETLAB+ server to provide assistance and troubleshooting. This access is usually performed over SSH on TCP port 22. If this port cannot be opened at the firewall, the administrator may authorize this access over the Remote Access Port (described in section 3.1). Customers who opt for beta software releases must have SSH enabled so that NDG can provide out-of-cycle spot patches; this cannot be done using the Remote Access Port.
NDG access via HTTP and one (1) remote access port is required by NDG to meet its support commitment. SSH is a requirement for NETLAB Professional Edition systems. SSH is not a requirement for NETLAB Academy Edition, however it is the preferred support protocol because SSH provides encryption.
NETLAB+ uses Ping when the administrator initiates an "outbound network test". Ping is used to verify reachability of the default gateway and the NDG CSS server. This test may fail if ICMP echo or echo-reply is blocked by an ACL or firewall. However, this will not cause a problem for NETLAB+ if all other protocols are working.
The NETLAB+ server uses the Internet to simplify administration of remotely accessible router equipment and to reduce the cost of ownership and support. NETLAB+ uses centralized support services to reduce the time, skills and budget necessary to operate and maintain a customized application running on an appliance based server. The Internet makes this possible.
Each NETLAB+ system is part of a centralized network management medium known as Central Support Services. Customers with a current support agreement receive the following services delivered through CSS:
All NETLAB+ systems have uniform hardware, software, and system configurations. Software updates and configurations are maintained through CSS. Using a centralized approach and Internet connectivity, the typical software update cycle is reduced from months to minutes. Uniformity among systems combined with CSS removes the need for operating system level access and manual configuration. All local system administration and configuration is performed through a web interface.
All CSS communication is "demand pull." All requests are initiated (outbound) from the NETLAB+ server. The HTTP protocol is used because it is generally allowed outbound by network security policies.
Because the Internet is an integral part of NETLAB+'s operation and support, certain connectivity requirements and protocols are necessary to maintain a functional system. These are described in section 2 and section 3. Please review these requirements with your network administrator.
Each NETLAB+ server uses the Internet to download and upgrade software packages. A package can contain software upgrades, lab updates, security patches, configuration changes, and bug fixes. The software update process can be executed automatically or manually. In automatic mode, NETLAB+ will check for updates. If new packages are available, the NETLAB+ server will download and install each package when the lab is not in use.
Keeping up with security advisories is usually a significant part of a system administrator's job. To simplify this task, NETLAB+'s integrity checks perform the following functions:
If a security problem is detected, an alert is sent to CSS for analysis and follow up by NDG. This method allows rapid response to security issues.
NETLAB+ stores all dynamic data in an SQL database. If the administrator enables automated backups, a daily backup of the database is stored on the NDG CSS server. The last 5 backups from each NETLAB+ system are stored on the CSS. In the event of a hardware failure, the database can be restored by NDG on a replacement system or hard drive. Using this method, a NETLAB+ site does not need to develop and maintain a separate backup server and methodology.
Each system provides status reports and alerts to CSS. This strategy provides useful information to support engineers and developers and significantly reduces support call detective work. The direct result is faster problem resolution and better service.
Each NETLAB+ system can keep the date and time synchronized through CSS. This insures that each NETLAB+ system has the correct date and time without administrative action.