NETLAB+ support materials for CCNA Security have been revised to provide compatibility with CCNA Security version V1.2. All labs are compatible with the MAP with ASA topology, as noted in the table below.
CCNA Security V1.2 labs require different console and enable secret password settings from other courses. Please review the information on enabling CCNA Security V1.2 labs.
| Lab | Description | Pod Required | Comments |
|---|---|---|---|
| 1.5.1.1 | Researching Network Attacks and Security Audit Tools | No equipment required. | |
| 2.5.1.1 | Securing the Router for Administrative Access | MAP w/ASA or MAP | |
| 3.6.1.1 | Securing Administrative Access Using AAA and RADIUS | MAP w/ASA or MAP | |
| 4.4.1.1 | Configuring Zone-Based Policy Firewalls | MAP w/ASA or MAP | |
| 5.5.1.1 | Configuring an Intrusion Prevention System (IPS) Using the CLI and CCP | MAP w/ASA or MAP | |
| 6.5.1.1 | Securing Layer 2 Switches | MAP w/ASA or MAP | 7.5.1.1 | Exploring Encryption Methods | No equipment required. |
| 8.7.1.1 | Configuring a Site-to-Site VPN Using Cisco IOS and CCP | MAP w/ASA or MAP | |
| 8.7.1.2 | Configuring a Remote Access VPN Server and Client | MAP w/ASA or MAP | |
| 8.7.1.3 | (Optional) Configuring a Remote Access VPN Server and Client | MAP w/ASA or MAP | |
| 9.4.1.1 | Configuring ASA Basic Settings and Firewall Using CLI | MAP w/ASA | |
| 9.4.1.2 | Configuring ASA Basic Settings and Firewall Using ASDM | MAP w/ASA | |
| 9.4.1.3 | Configuring Clientless and AnyConnect Remote Access SSL VPNs Using ASDM | MAP w/ASA | |
| 9.4.1.4 | Configuring a Site-to-Site IPsec VPN Using CCP and ASDM | MAP w/ASA | |
| 10.8.1.1 | CCNA Security Comprehensive | MAP w/ASA |
CCNA Security V1.2 labs require different console and enable secret password settings from other courses. If CCNA Security V1.2 and other courses are enabled in the same class, it is likely that the NETLAB+ automation will fail to save configuration files, since the default passwords, cisco and class are not the correct passwords for CCNA Security.
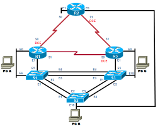
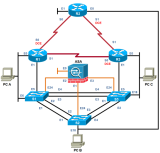
To avoid configuration management problems, we recommend that the CCNA Security V1.2 course be enabled in a separate class from other courses. Enabling this course within a separate class will allow you to set the appropriate console and enable secret passwords in the class settings required for CCNA Security V1.2.
Create a new class to be used for the CCNA Security V1.2 Course using the following settings:
The pod types listed are also available for "pod-only" reservations. To enable pod-only reservations, select the check boxes for the following options in the class settings that are appropriate for the pods available on your system:
"Pod-only" reservations are not tied to specific lab exercises. Therefore, the pod will be configured using the default network configuration and will not be properly configured to complete CCNA Security V1.2 labs.
Always select the correct lab exercise for the lab being performed. Students or teams should schedule the correct lab exercise from the catalog. NETLAB+ will only show those labs for which the required pod type is available. A lab that works on different pod types may appear more than once if your system is so equipped. Instructors should select the correct lab from the Exercise tab during instructor-led lab reservations. This can be done as many times as needed during the reservation.
Importance of Choosing the Correct Lab Exercise
Several of the labs may differ from the standard pod topologies. This is handled by NETLAB+ Dynamic VLAN Mapping technology. Always select the correct lab exercise for the actual lab. This insures that NETLAB+ will set up VLANs on the control switch such that lab devices and PCs are placed in the correct LAN segment for the exercise being performed. Selecting the correct exercise will also make the completed lab output easier to find in the archive.
NETLAB+ will configure the routers and switches with initial configuration files that include basic IP connectivity. Please verify this configuration by pinging the network interfaces before starting the lab exercise.
The routers used must meet minimum IOS requirements specified by the curriculum. The following recommendations are based on the CCNA Security V1.2 Equipment List (available on Academy Connection). Other routers and switches models may be used. Please consult Academy Connection NetAcad Maintenance - Image & Hardware Support Assistance with Legacy Equipment and Software.
| Router / Switch |
Recommended Model(s) |
Minimum DRAM |
Minimum Flash |
Minimum IOS |
Feature Set |
|---|---|---|---|---|---|
| R1 | CISCO1941-SEC/K9 | 512 MB | 256 MB | 15.1(4)M8 | Advanced IP Services w/ Security Technology Package License |
| R2 | CISCO1941-K9 | 512 MB | 256 MB | 15.1(4)M8 | Advanced IP Services |
| R3 | CISCO1941-SEC/K9 | 512 MB | 256 MB | 15.1(4)M8 | Advanced IP Services w/ Security Technology Package License |
| S1 | WS-C2960+24TC-L | 15.0(2)SE4 | LAN Base w/ cryptography IOS image for SSH support | ||
| S2 | WS-C2960+24TC-L | 15.0(2)SE4 | LAN Base w/ cryptography IOS image for SSH support | ||
| S3 | WS-C2960+24TC-L | 15.0(2)SE4 | LAN Base w/ cryptography IOS image for SSH support |
The ASA is required in order to complete Labs 9.4.1.1, 9.4.1.2, 9.4.1.3, 9.4.1.4 and 10.8.1.1 as noted in the pod compatibility table above. These 5 labs are the only CCNA Security V1.2 that require the MAP w/ASA.
Please refer to the Multi-purpose Academy Pod with ASA page for details on implementation.
| Device | Recommended Model(s) |
Minimum DRAM |
Minimum Flash |
Recommended IOS Feature Set |
|---|---|---|---|---|
| ASA | Cisco ASA5505-BUN-K9 | 512 MB | 128 MB | Cisco (ASA) Software Version 8.4(2) Base License Cisco ASDM Version 7.2(1) |
| Software Name | Purpose | Requirements | Comments / Links |
|---|---|---|---|
| Cisco Configuration Professional (CCP) V2.5 | CCP is installed in the PCs. |
Supported Microsoft Windows O/S:
|
When using CCP:
|
| Kiwi Syslog | This software will be used as the syslog server. Tftpd32 can also be used as the syslog server. |
Supported O/S:
|
www.kiwisyslog.com |
| Wireshark | This software will be used as the sniffer and packet analyzer. | Windows/Linux | www.wireshark.org |
| WinRadius | WinRadius is a standard RADIUS server for network authentication and accounting. | Windows/Linux | sourceforge.net/projects/winradius/ |
| NMAP/ZENMAP | This software is used to test the lab configuration. | Windows/Linux | www.insecure.org |
| Cisco VPN Client | This software is used to build a VPN. | www.cisco.com | |
| Tera Term Pro V2.3 | Software terminal emulator for Windows. | www.ayera.com/teraterm/ | |
| TFTP32 | DHCP, TFTP, SMTP, Syslog servers, and TFTP client. | http://tftpd32.jounin.net/tftpd32_download.html | |
| IOS-Sxxx-CLI.pkg | This file is used with Lab 5.5.1.1. | To obtain instructions on the file version and how to download, please see Lab 5.5.1.1. | |
| realm-cisco.pub.key.txt | This file is used with Lab 5.5.1.1. | To obtain instructions on the file version and how to download, please see Lab 5.5.1.1. | |
| PuTTY SSH Client | Used as an SSH Client | Windows/Linux | www.chiark.greenend.org.uk/~sgtatham/putty/ |